In the last post, I explained how a Network engineer can start a
security Domain & what is the prerequisite, top firewalls & Security
certifications.
In today's discussion below are our targets
· What is Firewall & its different types
· What is Zone, Trust, Untrust & DMZ Zone
· Why DMZ Zone if we have a LAN zone
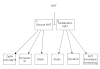
Firewall:
Software code can be run on Hardware or the cloud, Main function
of the firewall is traffic controlling & inspection., it can be Hardware
Device or Software base that can be installed as a VM.
Below is the different type of Firewalls
1. First
Generation
2. Second
Generation
3. Third
Generation (Next Generation NGFW)
First Generation: (Stateless FW)
In this type of FW, the traffic controlling is based on IP
address, Protocol like TCP, UDP
·
& Port number.
·
Comparing source/Destination address, and port number with the
configured policy then allow or block the traffic.
·
Verification & checking of each packet passes through Firewall
& due to this speed performance is affecting & slow.
·
Not checking the content of traffic & session details about
host/server connection. That's why also called Stateless Firewall
Second Generation: (Stateful FW)
In this firewall, all feature same as above first-generation FW
Plus Below extra capabilities
·
Maintain session information b/w two hosts communicating with each
other. That's why called Stateful Firewall.
·
After initial connection b/w host then its not checking any packet
that's why performance is fast.
Third Generation: (Next generation FW)
This firewall includes all features in the above two types of
firewalls Plus Below extra features.
·
Also called an application firewall as it checks all Layer 7
information.
·
Inspect content of traffic & compare it with configured
policy.
·
Contain User/content/application base filtering
·
Comparing traffic with defined signature to detect exploit,
malware & application using no standard ports.
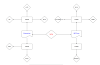
Zone:
It is the combination of interface/ports & logical grouping of
traffic.
Zone name can be any, but same nature interface put in same zone.
For example, create a zone give name Trust & put all LAN interfaces. Same
for WAN side Untrust Zone & put WAN interfaces.
For our easy & understanding normally LAN side interfaces are
part of the Trust Zone & WAN side is Untrust Zone.
1. Trust
2. Untrust
3. DMZ
Demilitarized Zone (DMZ):
All internet/public facing server are part of DMZ Zone. As nature
of these types of servers is that anyone from internet can access server. If we
put this Server in LAN Zone then all internet users can access & reachable
to our LAN due to these servers & this is Critical for our organization
resources & server also easy for attackers to get access.
Above is the reason that Public accessible server put in DMZ &
Organization resources in LAN for security purposes. Because by default traffic
is not allowed b/w inter Zone LAN & DMZ.
Interview Questions:
· What is Zone in Firewall?
· What is DMZ?
· How many generations of firewalls?
· What is meant by Next Generations Firewall?
· 2nd generation Vs Next Generation
Firewall?
· Difference between Stateless & Stateful
Firewall?
Keep Learning, Keep Reading, Keep Growing. IT
& IP is the future





0 Comments